ICS/SCADA CYBERSECURITY
ICS/SCADA Consulting
A Global Threat That We Can Control
Industrial fourth revolution technologies make an organization most vulnerable, and the impact is invariably devasting. That is unless security solutions are as innovative and robust as the technology itself. At CTI Resources, we deliver a new approach to security by protecting enterprise applications from the inside against today’s most dangerous cyber threats. With Virsec, CTI Resources expert and professional partner will eliminate your security blind spot! Our system provides real runtime protection – making sure your business-critical applications only execute correctly and never go off the rails, then security becomes manageable.
Our ICS solutions provide disruptive cybersecurity that safeguards ICS/SCADA/IT/OT systems from advanced targeted cyberattacks that enter the system without a trace to affect processes, registries, libraries, and memory. It protects vulnerable IT/OT/ICS systems with three flexible software options. As a result, you may defense your organization against advanced attacks that aren’t commonly detected by traditional security solutions.
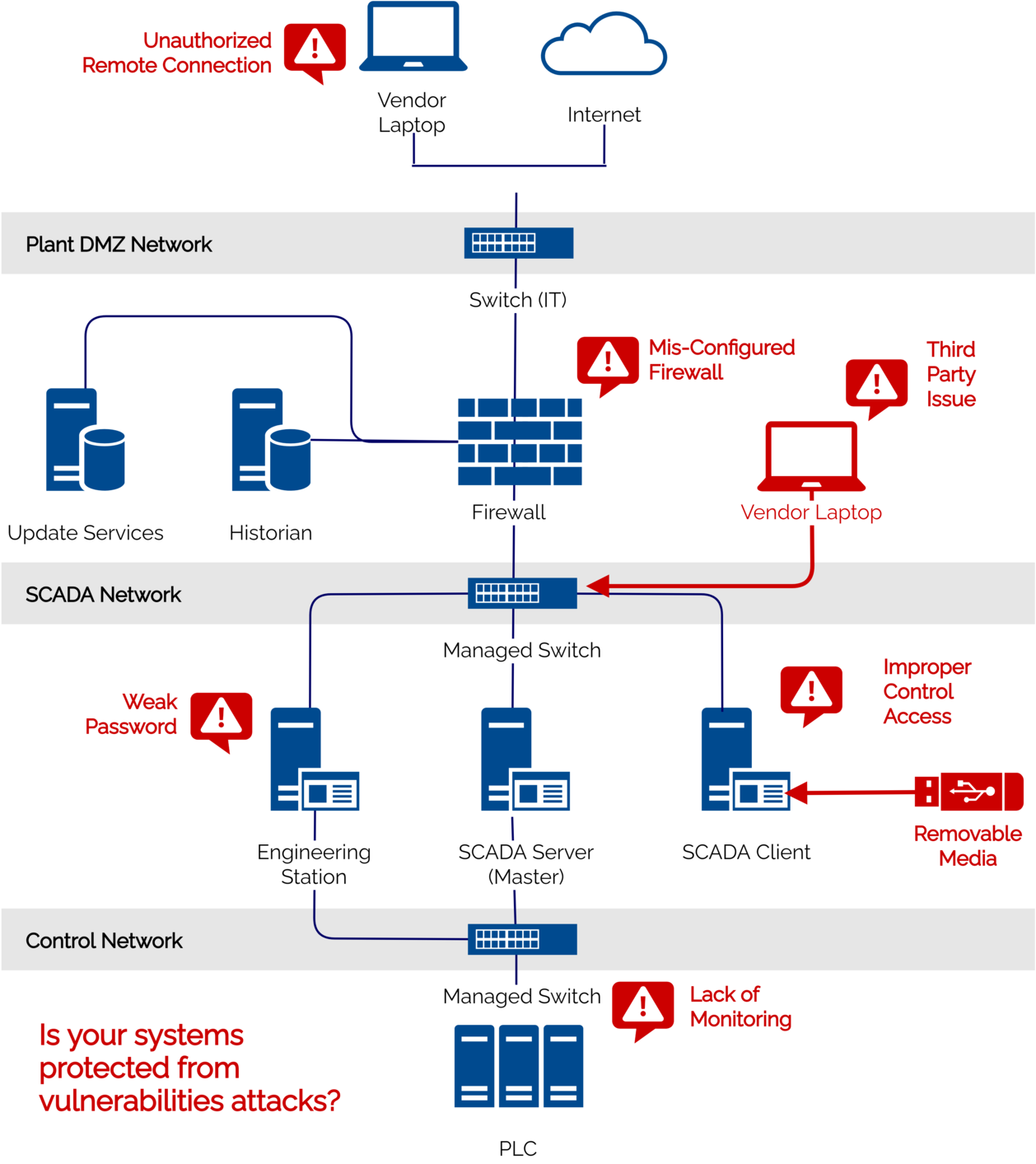
Why do Attackers Target Industrial Control Systems?
Attackers have different motives when deciding which environment to target. These attackers frequently have a financial incentive, a political purpose, or even a military goal in mind when they carry out attacks. Attacks might be state-sponsored, but they also might originate from rival companies, employees with nefarious intentions, or even hacktivists.
Depending on how they are configured and used, ICS environments may have vulnerabilities and threats. The Internet of Things (IIoT) devices and other contemporary systems and tools that have been added to the ICS environment to replace their older systems may offer greater openings for hackers to exploit.
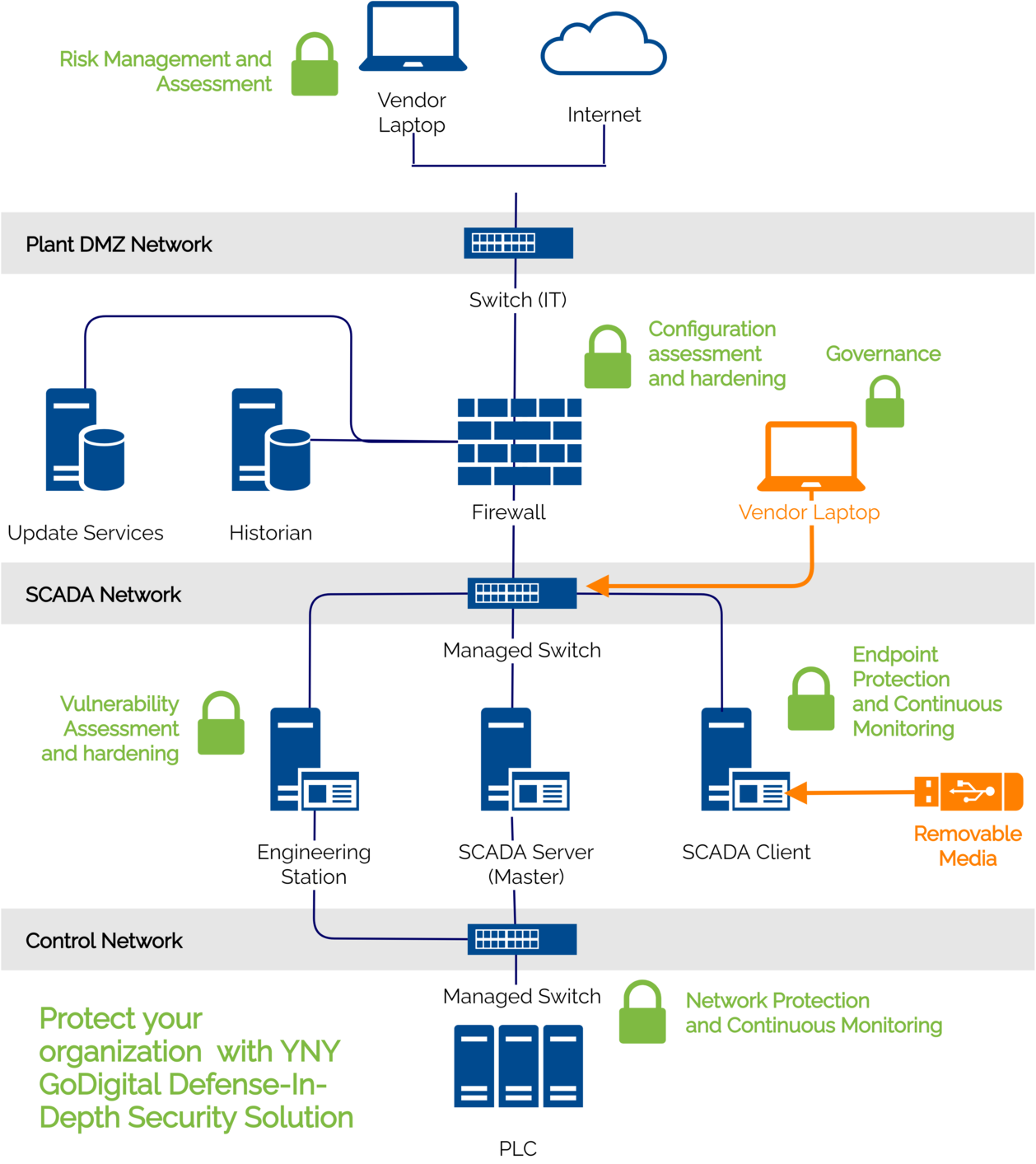
We cover Cybersecurity Solutions in three key areas
Process, People, and Technology.
We also cover
Cybersecurity Awareness Training
For people to aware of cyberattacks as well as Cybersecurity Solutions. These in-depth defenses solution provides CII owner in cybersecurity identification, protection, detection, and response. Our advanced technology uses a revolutionary deterministic approach to threat detection that stops complex and sophisticated attacks on critical application in real–time with near 100% accuracy. Learn more about our software and select the option that’s right for you.





